- Builder Pattern
Thursday, November 26, 2015
Wednesday, November 25, 2015
Common Commands
- features:addUrl mvn:org.fusesource.sparks.fuse-webinars.cxf-webinars/customer-features/1.1.4/xml
- features:list | grep customer
- features:listrepositories
- features:install activemq-camel
- osgi:install mvn:com.amtex/rdip/1.0.0-SNAPSHOT
- osgi:start 282
- osgi:stop 282
- osgi:uninstall 282
- osgi:update 282
- Deploying plain jar files
- osgi:install wrap:mvn:commons-dbcp/commons-dbcp/1.4
- osgi:install wrap:file:c:/ujjalb/data/backup/db2jcc4.jar
- log:display
- mvn eclipse:eclipse
- generate an eclipse project
- mvn clean compile exec:java -Dexec.mainClass=camelinaction.GreetMeBean
- - compile and run the Java class
- mvn clean compile camel:run
- mvn test -Dtest=OrderToCSVProcessorTest
- run a test
Important personalities in Microservices / DSL
- http://martinfowler.com/dsl.html
- Book - DSL in Action - https://www.manning.com/books/dsls-in-action
- Blog - - http://debasishg.blogspot.com/
- Book - Building Microservices - http://shop.oreilly.com/product/0636920033158.do
- https://www.thoughtworks.com/profiles/sam-newman
- Book - Camel in Action
- Book - Camel in Action
- Author of Camel, Active MQ, and many more
- Spring in Action - https://www.manning.com/books/spring-in-action-fourth-edition
- Blog - https://spring.io/team/cwalls
- Book - Design patterns - Elements of Reusable Object Oriented Software -http://www.amazon.com/gp/product/0201633612
Thursday, September 24, 2015
What are the ESB implementation patterns and SOA in Datapower? (115/285 technotes for 2015)
Application Awareness in ESB
- Service Virtualization
- Improved Manageability - all the things below can be managed centrally
- style sheets
- security
- caching
- routing
- Monitoring and Managing messages as they flow on the bus
- Routing messages
- Converting Protocols
- Transformation
- Securing messages
- Providing connectivity to application services via open and propriety interfaces
- ESB general monitoring
- track messages as they flow through the Enterprise - determine where time and resources are being spent
- remote monitoring of Datapower appliances - using SNMP, WSDM, WS-Management and proprietary SOAP API.
- for end to end monitoring for the ESB as well as the services is to - integrate Enterprise Monitoring software through std protocols like SNMP and ARM - like ITCAM for SOA
- ESB service level management (SLA) via monitoring - this is one of the most important
- throttle (reject) and shape(delay) traffic based on patterns below
- Prioritization
- Count Monitors
- Duration Monitors
- protects the backend application resources when.
- application latency reaches a threshold
- processing latency reaches a threshold
- Quality of Service - able to prioritize some message based on the the SLA
- Support of specific functionality or affinity -
- some functionality provided in a particular version
- session may exist on a particular destination - requiring affinity based routing
- Different types of Routing
- Content based routing
- Context based routing
- Aggregation and Disaggregation
- need to move messages from one protocol to another
- web based scenario's are asynchronous, but back end systems are transaction oriented and want it to be synchronous. So state management responsibility is also there for the mediator.
- if Websphere ESB is used - to convert protocol and transform and route message - it in general degrades performance
- XML-to-XML Transformations
- HTML/SOAP to XML Transformations
- Binary Transformations
- Content Enrichment and Filtering
Securing Messages -
- Though it has a large set of Security services - but a fairly small set of Services should be available for an ESB
- Support for standard WS-Security protocols as defined in the WS-I Basic Security Profile
- Support for credential mapping across multiple protocols and transports
- AAA
Connectivity -
Wednesday, September 23, 2015
What is a DMZ? (113/295 technotes for 2015)
In computer security, a DMZ or demilitarized zone (sometimes referred to as a perimeter network) is a
- physical or logical subnetwork that
- contains and exposes an organization's external-facing services to a larger and untrusted network, usually the Internet.
How can Datapower be used as an ESB? (112/285 technotes for 2015)
- supports - abstraction using the proxy architecture
- highly message oriented - with support for SOAP, raw XML and ther formats
- has full Web Services support
- Is network aware - residing between application layer and network - with support for
- routing, msg filter, transformation etc
- Also
- has a surprisingly small footprint
- built from the ground up to be network aware.
What are the different Datapower security scenarios? (111/285 technotes for 2015)
- Datapower typical security - solves the issues below
- Cross Enterprise Inter-operation -
- Federated Interoperability -
- Human and automated service invocations -
- Dynamic service binding -
- Global architecture layers impact -
- Datapower as a XML firewall
- While developing internet facing applications, the concept of DMZ is very important - this is the place where a hardened bastion host is placed between 2 firewalls.
- Below is the standard topology - without Datapower
- The WebServer - does almost nothing
- Most of the work is done by Webservices Gateway
- Using It is the most hardened device available in the market.
- the role of Datapower within the DMZ is that it needs to be able to stop any incoming request and provide authentication and authorization - depending on Business Requirements.
- Eliminates the Web Server and the Web Services Gateway
- More secure - easy to manage
- Below are a few of the protection which Datapower provides -
- XDOS
- well formedness
- verify digital signature
- signing messages
- implementing service utilization to mask internal resources via XML transformation and routing
- encrypting data at the field level
- Three basic types of Firewall
- Static backend
- Dynamic backend
- Loopback
- Recommendation: All internet-facing systems that provide for inbound Web services, requests should use Datapower as their XML firewall, even when performance or security is considered unimportant.
- Recommendation: DataPower should be used as the policy enforcement point for Web services authorization. It should interact with a central policy decision point, such as Tivoli Access Manager.
Monday, September 21, 2015
What is IBM Tivoli? (110/285 technotes for 2015)
- Policy management: WS-Policy, WS-SecurityPolicy
- Federated Identity Management: Liberty, SAML 2.0, WS-Federation, WS-Security
- Auditing and compliance for SOA: Compliance Automation)
- User provisioning: WS-Provisioning/SPML 2.0.
- In order to connect to TAM from DP, a TAM client must be configured in the DP SOA appliance.
- TAM is specified in the AAA policy.
What are the mechanisms supported by AAA (109/285 technotes for 2015)?
- SAML
- SAML, a user can login to one system in an environment, and then will be able access to other systems in that environment without needing to login again (until the web browser session is ended).
- XACML PEP/PDP -
- eXtensible Access Control Markup Language
- Policy Enforcement Point/ Policy Decision Point
- The standard defines a declarative access control policy language implemented in XML and a processing model describing how to evaluate access requests according to the rules defined in policies.
- Kerberos & SPNEGO
- a protocol for authentication
- uses tickets to authenticate
- avoids storing passwords locally or sending them over the internet
- involves a trusted 3rd-party
- built on symmetric-key cryptography
- Kerberos is normally deployed in a client/server environment. It is rarely used in web-applications and thin client environments.
- Because of this, SPNEGO comes to the rescue. It stands for Simple and Protected GSS-API Negotiation Mechanism, which provides a mechanism for extending a Kerberos based single sign-on environment to web-applications.
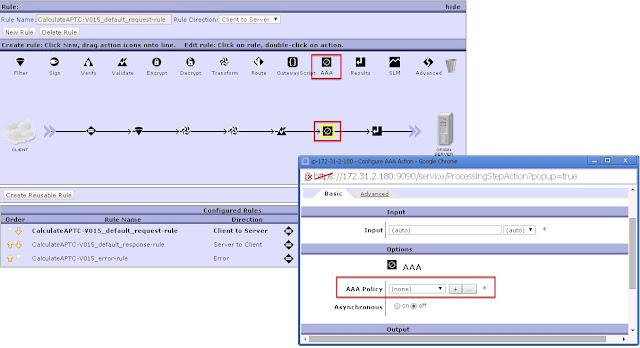
What is a multistep probe? What is a AAA action?(108/285 technotes for 2015)
To view the contents of any phase, enable the multi-step probe for the firewall or Web Services proxy - employing a document processing policy containing a AAA action
AAA Action :
AAA Action is a Datapower object - that references a specific AAA policy. This is the way to add (bridge) a AAA policy to any of the services mentioned below.
- XML Firewall
- MPGW
- Web Service proxy
- XSL proxy
What is AAA? (107/285 technotes for 2015)
- Authentication
- Authorization
- Auditing
- Extract identity (EI) claim - such as username /password from HTTP basic authentication.
- Extract resource (ER) - such as Web services URL being accessed.
- Authenticates (AU) the extracted identity - with either an on-board / off-board identity server - LDAP
- Map Credentials (MC)- using rewrite rules
- Map Resource (MR) - mapped using rewrite rules
- Authorize (AU)- submit to a policy server for authorization.
- Post Processing (PP) - audit
What is Credential Transformation in Datapower? (106/285 technotes for 2015)
Types of Transformation:
- Technology -
- changing a credential from one type to another
- eg: sender might use Digital Signatures, while the receiver might use Username token.
- Naming -
- the name that represents a user might change, similar to Relationship in Process Server.
- eg: your identity to IBM can be your serial number, but to bank it can be bank account number.
- Custom developed ad-hoc code -
- Datapower can perform complex transformations - using built in functions as well as custom transformations.
- Leverage a product like TFIM (Tivoli Federated Identity Manager)
- Datapower can also connect to products like TFIM.
- Use Datapower - for simple credential transformation
- User TFIM -
- for complex credential transformation
- when transformation occurs in multiple places like Datapower and WAS.
How does Datapower provides Acceleration and Flexibility? (105/285 technotes for 2015)
Datapower consumes messages in the network speed, and can remove the WS-Security overhead and pass the clear message to back-end server and vice versa.
Felxibility -
- Datapower supports more of WS-Security than of any Application Server - maybe Websphere will catchup the near future, but as of now they have a complete coverage.
- Datapower fundamentally includes XSL processing engine - which helps in easy Transformation of messages.
- By offloading the WS-Security processing to Datapower, we eliminate the need to configure and re-configure the back end server.
- Client who want to use WS-Security but find that their Application Server, does not fully support this, should evaluate Datapower.
- Clients expecting to frequently change WS-Security settings,
- Clients with problematic messages.
Sunday, September 20, 2015
What is WS Trust & Secure Conversation? (104/285 tech notes for 2015)
WS-Security adds enterprise-level security features to SOAP message exchanges, but with a substantial performance cost.
WS-Trust builds on WS-Security to provide a way of exchanging security tokens,
WS-SecureConversation builds on WS-Security and WS-Trust to improve performance for ongoing message exchanges
What is the performance issue with WS Security?
WS Security uses asymmetric keys - that is public and private key pair, which require larger keys and complex processing while decrypting messages vs single secret keys known to the both parties.
WS Conversation uses WS Trust (+ WS Security) to use only a single key pair to communicate between client and server.
What is WS-Trust?
WS Trust is a WS based standard for Requesting / Receiving the tokens
- Function 1 - Implement the STS to
- issuing
- renew
- cancel
- validate Security Tokens
- Function 2 - Support brokering Trust relationship
-----------------------
- Consumer Requests a Security Token (RST) to the STS
- STS returns a signed token to the Consumer - Request Security Token Response (RSTR)
- Once the token is received - the requester can present it to multiple services.
References:
http://www.ibm.com/developerworks/library/j-jws15/
https://www.youtube.com/watch?v=YZNVyUc-3fQ
http://bit.ly/1WcpDKb
Saturday, September 19, 2015
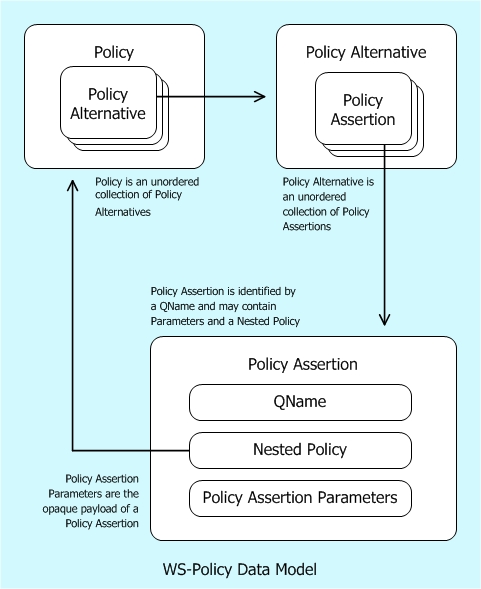
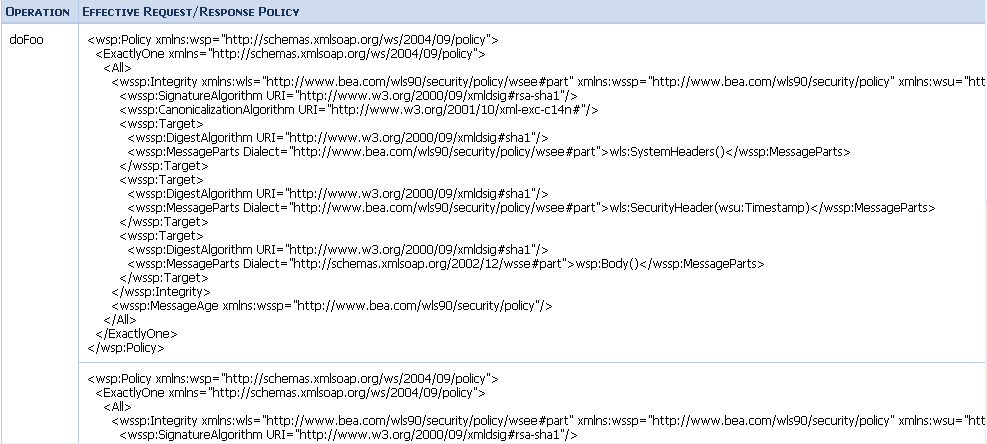
What is WS Policy? (103/285 technotes for 2015)
- capabilities
- requirements
- general characteristics of entities in an
- Security
- Privacy
- Reliable Messaging
- https://www.youtube.com/watch?v=vh4gYKe3_Jc
- www.redbooks.ibm.com/redbooks/pdfs/sg247620.pdf
- http://www.w3.org/TR/ws-policy-primer/
Thursday, August 20, 2015
Why is Messaging considered superior to Shared DB? Messaging vs Shared DB?(102/285 tech notesfor 2015)
If you are building a simple application with low traffic, there is
something to be said about keeping another component out of your system. It
is very likely not using a message bus is the right answer for you.
However, I would suggest building your system in a way you could swap out
the database based queue system for middleware solution. I agree with the
article. A database is not the right tool for queue based system, but it
may be good enough for you.
Advantages of Queue based systems:
Queue based system like RabbitMq are built around massive scale on moderate
hardware. Their architecture is able to achieve this by avoiding processes
which make ACID compliant database system slow by their nature. Since a
Message bus -
only needs to ensure a message is stored and successfully processed,
it doesn’t need to bother with locking and writing transaction logs.
Both of these concepts are absolutely required for an ACID system but are
often a cause of contention.
Issue with DB:
Performance wise it comes down to, you have a SQL table. Lots of reads and
lots of writes. Both require some sort of locking to update rows, pages and
indexes. Your polling mechanisms is constantly locking an index to do look
ups on it. This prevents writes from happening, at best they are queued.
The code doing the processing is also locking to update the status on the
queue as they complete or fail. Yes, you can do query optimization after
optimization to get this to work, or you can use a system specifically
designed for the work load you are asking.
A RabbitMq eats up this type of workload without even breaking a sweat.
On top of that you get to save your database from the workload giving it
more room to scale doing other things.
Polling:
Another thing to consider is most queue system typically do not use a
polling technique (some allow for HTTP, but recommend to avoid using for
the receive side). RabbitMq uses network protocols specifically designed
for message buses such as AMPQ.
References:
http://mikehadlow.blogspot.fr/2012/04/database-as-queue-anti-pattern.html
brianfeucht in stackoverflow -
http://programmers.stackexchange.com/questions/231410/why-database-as-queue-so-bad
Why is Messaging considered superior to Shared DB (102/285 technotes for 2015)
If you are building a simple application with low traffic, there is something to be said about keeping another component out of your system. It is very likely not using a message bus is the right answer for you.
Friday, August 14, 2015
How To Set Up GUI On Amazon EC2 Ubuntu server?(101/285 technotes for 2015).
-------------------------------
This can be done. Following are the steps to setup the GUI
* Create new user with password login
How To Set Up GUI On Amazon EC2 Ubuntu server?(101/285 technotes for 2015).
This was published in http://bit.ly/1LaP9tT. Based on the comments and minor changes (maked in bold) the below worked for me.
This can be done. Following are the steps to setup the GUI
* Create new user with password login
sudo useradd -m awsgui
sudo passwd awsgui
sudo usermod -aG admin awsguisu - awsgui
sudo vim /etc/ssh/sshd_config # edit line "PasswordAuthentication" to yes
sudo /etc/init.d/ssh restart
* Setting up ui based ubuntu machine on AWS.
* In security group open port 5901. Then ssh to the server instance. Run following commands to install ui and vnc server:
sudo apt-get update
sudo apt-get install ubuntu-desktop
sudo apt-get install vnc4server
* Then run following commands and enter the login password for vnc connection:
vncserver
vncserver -kill :1
vim awsgui/.vnc/xstartup
* replace the text with the text below (make sure u have a copy)
#!/bin/sh
def
export XKL_XMODMAP_DISABLE=1
unset SESSION_MANAGER
unset DBUS_SESSION_BUS_ADDRESS
gnome-panel &
gnome-settings-daemon &
metacity &
nautilus &
gnome-terminal &
* When you’re done, hit Ctrl + C on the keyboard, type :wq and hit Enter.
* Restart the server
* Then start vnc server again.
vncserver
In the vnc client, give public DNS plus “:1” (e.g. www.example.com:1) or private ip address. Enter the vnc login password. Make sure to use a normal connection. Don’t use the key files.
Thursday, August 6, 2015
ParseMFCFile.java (101/285 technotes for 2015)
name=“callAddressValidation”
Req:{Trace=5, Input=1, XSLTransformation=3, BOMapper=3, Stop=3, InputFault=1, ServiceInvoke=3, InputResponse=1, CustomMediation=5}
Err:{Trace=1, XSLTransformation=1, BOMapper=1, Stop=1, InputFault=1, ServiceInvoke=1, ErrorInput=1, InputResponse=1, CustomMediation=1}
name=“findStateCountyCity”
Req:{Trace=3, Input=1, BOMapper=2, XSLTransformation=2, Stop=1, InputFault=1, ServiceInvoke=1, Callout=1, InputResponse=1, CustomMediation=4}
Res:{InputFault=1, InputResponse=1}
Err:{Trace=1, XSLTransformation=1, BOMapper=1, Stop=1, InputFault=1, ServiceInvoke=1, ErrorInput=1, InputResponse=1, CustomMediation=1}
ParseMFCFile.java (101/285 technotes for 2015)
Friday, July 31, 2015
The declared package does not match the expected package “”? (100/285 technotes for 2015)
The issue description:
The declared package “org.jboss.as.quickstarts.helloworld” does not match the expected package “main.java.org.jboss.as.quickstarts.helloworld” HelloService.java /jboss-helloworld/src/main/java/org/jboss/as/quickstarts/helloworld line 17 Java Problem
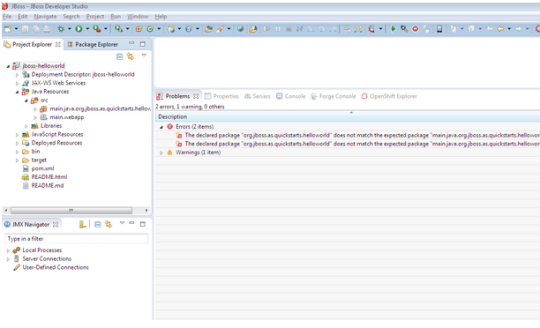
Resolution:
To resolve this issue.
Right click on the the project → Properties → Java Build Path → Source
Click on the project →
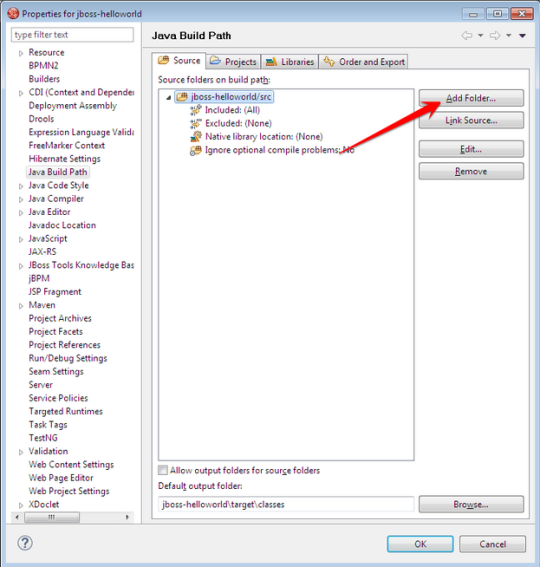
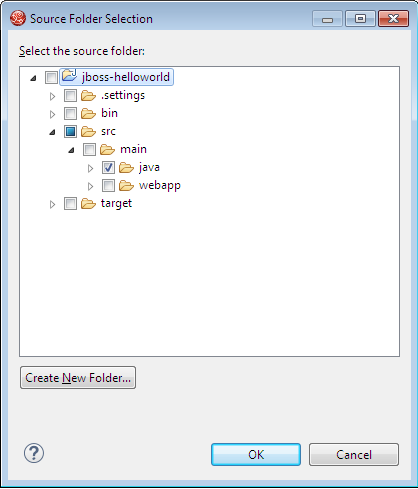
Add a new Source folder src/main/java
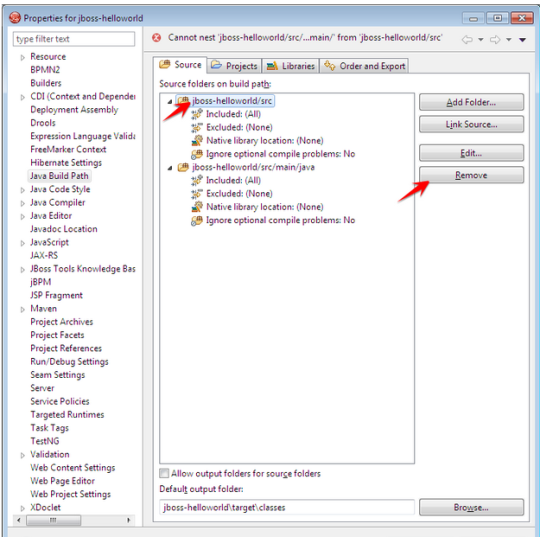
Remove the old src folder
Thursday, July 30, 2015
What is JBOSS EAP? (99/285 technotes for 2015)
- JBoss.org Application Server/Clustering project,
- JBoss Hibernate Framework,
- JBoss Seam Framework into a single distribution with a single patch and update stream, multi-year maintenance policy.
JBoss EAP is certified on 17 operating systems, 5 Database Management systems and JVM combinations. It also integrates with
Advantages:
- 0 licence fee, significantly lower Total Cost of Ownership (TCO)- upto 70% savings.
- avoid vendor lock in ?????
With 24x7x365 support with 1 hour SLA you are guaranteed support when you need it.
Monday, July 27, 2015
Useful Java syntaxes.
org.apache.commons.lang3.Validate
This class assists in validating arguments. The validation methods are based along the following principles:
- An invalid
nullargument causes aNullPointerException. - A non-
nullargument causes anIllegalArgumentException. - An invalid index into an array/collection/map/string causes an
IndexOutOfBoundsException
———————————————————————————
Wednesday, July 22, 2015
What is the difference between JAXB and JAXP? (98/285 technotes for 2015)
JAXP (Java API for XML Processing) is a rather outdated umbrella term covering the various low-level XML APIs in JavaSE, such as DOM, SAX and StAX.
- Create a SAX Parser or DOM Parser and then PArse the data, if we use DOM, it may be memory intensive if the document is too big. Suppose if we use SAX parser, we need to identify the beginning of the document. When it encounters something significant (in SAX terms, an “event”) such as the start of an XML tag, or the text inside of a tag, it makes that data available to the calling application.
- Then Create a content handler that defines the methods to be notified by the parser when it encounters an event. These methods, known as callback methods, take the appropriate action on the data they receive.
JAXB (Java Architecture for XML Binding) is a specific API (the stuff under javax.xml.bind) that uses annotations to bind XML documents to a java object model.
- Bind the schema for the XML document.
- Unmarshal the document into Java content objects. The Java content objects represent the content and organization of the XML document, and are directly available to your program. After unmarshalling, your program can access and display the data in the XML document simply by accessing the data in the Java content objects and then displaying it. There is no need to create and use a parser and no need to write a content handler with callback methods. What this means is that developers can access and process XML data without having to know XML or XML processing
References:
http://stackoverflow.com/questions/2801502/what-is-the-difference-between-jaxp-and-jaxb
Increase Heap Memory in Websphere(97/285 technotes fpr 2015)
Method 1: Using the administrative console
Open the administrative console.
Navigate to Servers > Server Types > WebSphere application servers > <servername>
Navigate to Server Infrastructure > Java and Process Management > Process Definition
Navigate to Additional Properties > Java Virtual Machine > General Properties
Define the values (in MB) for ‘Maximum heap size’ and/or ‘Initial heap size’.
Restart the server.
Note: If the heap size is already low, the administrative console might not open. In such cases, use some other method to configure the heap size.
Method 2: By editing the configuration files
This method should be used with caution.
Search for a file named server.xml in your WebSphere installation.
Generally, the location of this file is as follows:
<profilehome>/config/cells/<cellname>/nodes/<nodename>/servers/<servername>/server.xml
Select the server.xml specific to your server and edit it to add/modify/delete the attributes @initialHeapSize and @maximumHeapSize of the element <jvmEntries> The value of these attributes is the heap size in MB.
For example:
<jvmEntries ... initialHeapSize="2048" maximumHeapSize="3072" ...>
...
</jvmEntries>
Restart the server after saving the changes to server.xml.
References:
Tuesday, July 21, 2015
SVN CLEANUP FAILS(96/285 technotes for 2015)
What to do is SVN Cleanup Fails? Please follow the guide lines below.
Prerequisites
- Download and unzip sqlite3 shell tool, e.g. sqlite-shell-win32-x86-3080803.zip
- Adjust paths in the commands below to match your environment
Fix (manual)
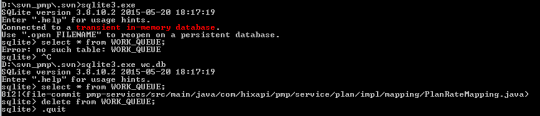
Run this if you just want to test if this helps
** I placed the sqllite3.exe in the same folder where we have wc.db
D:svn_pmp.svn>sqlite3.exe wc.db
SQLite version 3.8.10.2 2015-05-20 18:17:19
Enter “.help” for usage hints.
sqlite> select * from WORK_QUEUE;
812|(file-commit pmp-services/src/main/java/com/hixapi/pmp/service/plan/impl/mapping/PlanRateMapping.java)
sqlite> delete from WORK_QUEUE;
sqlite> .quit
Fix (automated)
If previous step worked for you, consider automating the process with these steps
- Go to your .svn folder, e.g.
D:svn_pmp.svn - Copy sqlite3 shell tool there
- Create a
fix-svn.batfile in that folder - Next time you need to fix it, just run the shortcut on your desktop
Insert scripting code, and adjust paths
"d:svn_pmp.svnsqlite3.exe" wc.db "delete from WORK_QUEUE"
"C:Program FilesTortoiseSVNbinsvn" cleanup "D:src"
Save bat file and make a shortcut to your desktop
References:
https://changilkim.wordpress.com/2012/12/10/svn-cleanup-fails/
http://stackoverflow.com/questions/18000363/tortoisesvn-wont-allow-me-to-add-any-files
Tuesday, July 7, 2015
Which ESB to choose? (95/285 technotes for 2015)
- first successful open source ESBs
- a commercial enterprise version is available - offers additional functionality and support for the product
- graphical editors for an efficient implementation of integration scenarios
- connectors for B2B products such as SAP or Salesforce
- functionality of a suite is missing in Mule ESB - products from other vendors has to be used
- small community, a restrictive licensing model and limited availability of the source code
- based on Eclipse and very intuitive.
- based on de facto standards in the integration environment such as Apache CXF and Apache Camel
- Based on the research by Forester - conducted by IBM - the performance and maturity of the product IBM IIB makes to significantly ahead of the game.
References:
http://www.infoq.com/articles/ESB-Integration
http://bit.ly/1JT0iz1 - in favour of IBM IIB
JBoss Fuse vs IBM ESB? (94/285 technotes for 2015)
- IBM products has a license cost and a support cost.
- JBoss does not have a License cost - but has a subscription cost. Red Hat JBoss Fuse subscription is over $823K less than IBM WebSphere Enterprise Service bus at list price—or just 7.3% of the IBM cost.
Click on the link to see how Google Trends shows the interest over the time between the two products and the latest Integration technology - Apache Camel (which is used in JBoss Fuse)
Websphere ESB vs (Jboss Fuse & Apache Camel) (live link)
Sample below - the blue line shows decrease in interest IBM WebSphere technologies

Support:
- RedHat JBoss Fuse can be used in any customer locations.
- The same is applicable for IBM ESB (except IBM WESB - Registry Edition or Retail Edition)
- RedHat JBoss Developer Studio is used for all Middleware development.
- Similarly IBM Websphere Integration Developer used for all development purpose. IBM tooling is more matured - but Red Hat is catching up.
- JBoss Fuse development is extremely flexible - developers can swtich between graphical and xml views. Developers can can write a Apache Camel entirely in Java.
- IBM does not encourage switching between gui mode and xml mode.
- With Red Hat Subscription, developers can choose to explore all the RedHat JBoss Middleware platforms like RedHat JBoss Data Grid and BRMS etc.
- This is not possible with IBM.
- RedHat JBoss uses Apache Camel - open source, out of the box, standards based integration patterns based out of the book - Enterprise Integration Patterns by Gregor Hohpe and Bobby Woolf.
- IBM WESB does not allow pattern based development
- RedHat JBoss Fuse requires 100mb free disk space and 2GB RAM. This can be even tuned and optimize.
- IBM in geneal required 6GB RAM to run IBM WESB (including IBM Application Server).
- Use the Camel core component of Red Hat JBoss Fuse to embed routes in Java applications. This kind of feature is not available in IBM ESB.
- RedHat JBoss Fuse uses ActiveMQ - an open source software with a very small footprint. ActiveMQ.
- It has several other benefits over IBM Websphere JMS. Please see link below for more info.
- RedHat JBoss Fuse supports all the different types of transport binding including HTTP, JMS, HTTPS, FTP.
- On top of that Camel provides 125 connectors to varied systems.
What are the components of JBoss Fuse? (93/285 technotes for 2015)
Apache Camel - is a
- 1. Simple
- 2. Modular
- 3. Open Source
- 4. Java Library
- Connecting various components together, provide transformation, implement routing and also include Business Logic.
- This is a rule based routing and mediation engine using EIPs (Enterprise Integration Patterns).
- Embed in any JVM and use any dependency injection framework
- Embed your integration solution directly where you need to.
- It has 100's of components already
- Huge community
- Also provide Domain Specific Language - you can use Java / Scala / ... or XML to decribe your flows
- For XML there is support for visual tooling
- open-source,
- fully featured Web services framework
- open source message broker written in Java together with a full
- Java Message Service (JMS) client.
- modern and
- polymorphic container. It’s a
- lightweight,
- powerful, and
- enterprise ready container powered by OSGi.
- You can deploy different kind of applications in Karaf, OSGi or non-OSGi.
- technology layer that allows a
- group of containers to form a cluster that
- shares a common set of configuration information and a
- common set of repositories from which to access run-time artifacts.
What is JBoss Fabric? (92/285 technotes for 2015)
Fuse Fabric is a runtime environment that leverages capabilities of Apache Karaf, the container underlying JBoss Fuse, to provide centralized configuration and provisioning capabilities. In brief, Fuse Fabric provides the ability to create container instances running locally or remotely, including on cloud environments like Amazon EC2 and Rackspace. You can then create and apply Profiles that define what OSGi bundles and associated configurations (name / value pairs) to apply to each managed container.
References:
https://github.com/FuseByExample/docs/blob/master/deploy-using-fabric/README.md
Tuesday, June 30, 2015
Datapower Setup in VMWare Workstation (91/285 technotes for 2015)
- Download the “idg7104.vmware_deved.ova” file (Datapower virtual appliance file) from the IBM Passport Advantage site.
- Download the VMWare Workstation 11 from http://vmw.re/1FsfizF
- Start VMWare Workstation - File–> Open –>
“idg7104.vmware_deved.ova” - Once the import is complete - start the appliance
- If required adjust the number of processors and memory Datapower uses.
Static IP:
Do you want to install Wizard? y
Step1:
Do you want to Configure network interfaces? y
Do you have this information? y
Do you want to configure the eth0 interface? y
Do you want to enable DHCP? n
Enter the IPv4 address for the interface in CIDR notation: 10.0.0.124/24
Enter the IPv4 address for the default gateway: 10.0.0.1
Do you want to configure the eth1 interface? n
Do you want to configure the eth2 interface? n
Do you want to configure the eth3 interface? n
Step2: Do you want to configure network interfaces? y
Do you want to configure DNS? y
Enter the IP Address of the DNS Server: 10.0.0.1 (this is the ip address of my default gateway)
Step3: Do you want to define a unique system identifier? y
Enter a unique system identifier: data123
Step 4 - Do you want to configure remote management access? y
Do you want to enable SSH? y
Enter the local IP address : 10.0.0.124 (this is the static ip for the DP)
Enter the port number: 22
Do you want to enable WebGUI access? y
Enter the local IP address : 10.0.0.124 (this is the static ip for the DP)
Enter the port number : 9090
Step5-7 - no
Saved the configuration
Post Installation:
Now goto internet browser and type the url
https://10.0.0.124:9090/login.xml?session=false
DHCP:
Do you want to install Wizard? y
Step1:
Do you want to Configure network interfaces? y
Do you have this information? y
Do you want to configure the eth0 interface? y
Do you want to enable DHCP? y
Do you want to configure the eth1 interface? n
Do you want to configure the eth2 interface? n
Do you want to configure the eth3 interface? n
Step2: Do you want to configure network interfaces? y
Do you want to configure DNS? n
Step3: Do you want to define a unique system identifier? y
Enter a unique system identifier: data767
Step 4 - Do you want to configure remote management access? y
Do you want to enable SSH? y
Enter the local IP address : 0.0.0.0 (this is the default ip)
Enter the port number: 22
Do you want to enable WebGUI access? y
Enter the local IP address : 0.0.0.0 (this is the default ip)
Enter the port number : 9090
Step5-7 - no
Saved the configuration
Post Installation:
cmd -> show int
this will give the ip address
Now goto internet browser and type the url
https://10.0.0.16:9090
If there is any issue with the DP Portal not working, login to CLI and type the command below
→ show int
If you dont see the ip address for eth0, type the commands below
→ co
→ ethe eth0
→ show
Check if the above value of ip-config-mode is static / dhcp. If static, set it to dhcp
→ ip-config-mode dhcp
→ exit
→ write mem
→ exit
→ show int
Thursday, May 28, 2015
If Workstation fails to load or you have issues using the Workstation UI. (90/285 technotes for 2015)
- Navigate to the VMware Workstation folder in Program Files.
- Double-click vm-support.vbs support script.
- When the process completes, you are presented with a message informing you that a file was created in a folder calledvmware-support in your host’s %TEMP% folder. The compressed support bundle name begins with vmsupport and includes a date stamp for month, day, and year.
- After collecting your support data, upload it as an attachment to your Support Request (SR). For more information, seeUploading diagnostic information to VMware (1008525).
References:
Complete article - http://vmw.re/1RrInD5
Wednesday, May 20, 2015
Creating Virtual NIC (Network Interface Card) using Microsoft Loopback Adapter.
- Under
hdwwiz.exe- … - - Select from list - Network Adapters, you should have a"Microsoft Loopback Adapter" device.
- Finish
References:
http://superuser.com/questions/339465/creating-a-virtual-nic-on-windows-7
What is Microsoft Wifi Mini Virtual Adapter? (88/285 technotes for 2015)
Virtual WiFi is a technology that virtualizes your network adapter much in the same way VMWare virtualizes your entire operating system. Once virtualized, you can basically convert one physical wireless adapter into two virtual ones
References:
Tuesday, May 19, 2015
Basic’s of Networking. (87/295 technotes for 2015)
What is a Public IP Address?

What is a Private IP Address?
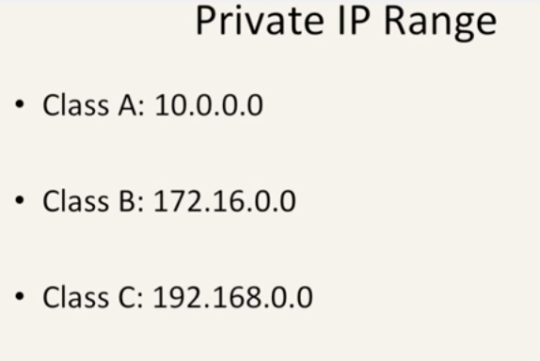
What is a Default Gateway?
Default Gateway - is a the device that passes information from the local subnet to some other subnet (local network to internet)
In home, the home router is assigned the default gateway ip address - 192.168.1.1
What is a CIDR Notation?
First address of a network, followed by a slash character (/), and ending with the bit-length of the prefix. For example, 192.168.1.0/24 is the prefix of the Internet Protocol Version 4 network starting at the given address, having 24 bits allocated for the network prefix, and the remaining 8 bits reserved for host addressing
What is a Subnet?
The practice of dividing a network into two or more networks is called subnetting.
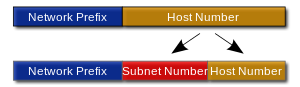
Subnets may be arranged logically in a hierarchical architecture, partitioning an organization’s network address space into a tree-like routing structure.
What is a Subnet Mask?
A subnet mask is a screen of numbers used for routing traffic within a subnet. Once a packet has arrived at an organization’s gateway or connection point with its unique network number, it can be routed to its destination within the organization’s internal gateways using the subnet number.
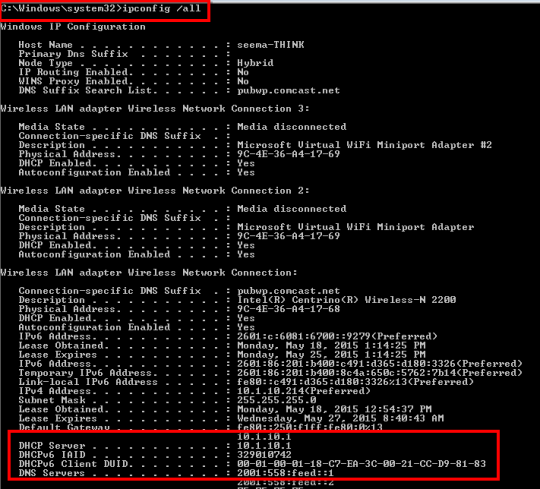
What is a DHCP Server?
Where is a DHCP Server located?
DHCP server is located in the Router. If you do ipconfig /all you will see any entry mentioning the DHCP entry.
Goto your browser and type the ip address of the DHCP Server -> it will take you to the router admin console
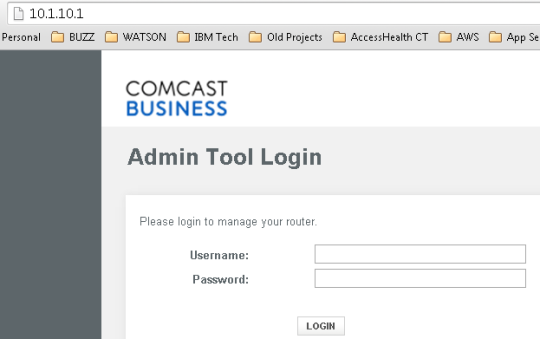
Most likely it will be the same as the default gateway.
What is a DNS Server?
Domain Name Servers (DNS) are the Internet’s equivalent of a phone book. They maintain a directory of domain names and translate them to Internet Protocol (IP) addresses. This is necessary because, although domain names are easy for people to remember, computers or machines, access websites based on IP addresses
Where is a DNS Server located?
DNS Server is a servics provided by the ISP - http://dns.comcast.net/
Some smart routers act as a local DNS Server by remembering ip addresses of a websites.
Command - ipconfig /all | findstr /R "DNS Servers"
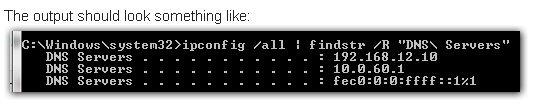
What is a primary DNS?
References:
- http://en.wikipedia.org/wiki/Subnetwork
- DHCP - http://bit.ly/1efyHgK
- Subnet - https://youtu.be/IDLrt-yppbI
- Command for DNS Server - http://bit.ly/1Fo51qB
- Router acting as DNS Server - http://bit.ly/1LlJhxD
Friday, May 15, 2015
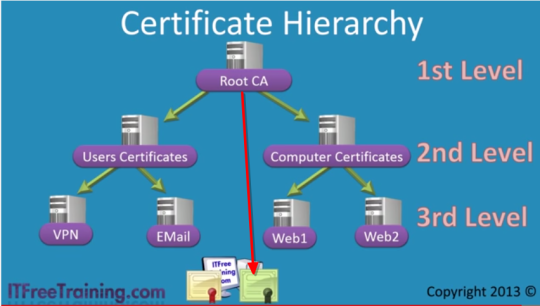
What is a Root CA and Intermediate Certificate? (86/285 technotes for 2015)
- The Root certificate has the private key issued by the CA (Certificate Authority).
- This is set offline and has to be in a secured location as it contains the private key.
- From the Root CA - 2nd Level / Intermediate Certificate’s are generated
- 2nd Level Certificates are responsible for issuing certificated to any websites which require certificates.
- In order for the browser accesing a website to trust a certificate, the browser has to be pre-loaded with the Root Certificate (the red arrow).
References:
Wednesday, May 13, 2015
IBM ODM Introduction (85/285 technotes for 2015)
Challenges Solved:
- Rules hidden in your application or processes - hard to find and change
- You want to Automate Operational Decisions - assuming safe
- Legacy system is hard to use - and not accessible by Business users
- Change requests often take months to implement
TIME TO SWITCH to ODM - ODM is all about CHANGE
- Rules that change
- Detect real time Business Events - apply rules accordingly
ODM (Operational Decision Management) system is the evolution of BRMS (Business Rules Management System).
- Easy to use system to automate day-to-day operational decisions
- Intuitive interface both for business and IT
References:
ODM for Dummies - http://ibm.co/1PjfJq6
Importing Image into AWS as an AMI using AWS CLI. (84/285 technotes for 2015)
Importing an external image into AWS requires the steps below.
- Download and install the AWS Command Line Interface.
- goto command prompt and
- make sure ec2 import-image command is avaliable
aws ec2 help
- Download the VM image from its current environment as an OVA file (or VMDK, VHD, or RAW).
- Upload the VM image to S3 using the web console. Goto S3 –> choose / create a bucket and upload the VM file.
- Once the VM image is uploaded, import your VM using the ec2 import-image command.
aws ec2 import-image –cli-input-json “
{ "Description": "Datapower OVA",
"DiskContainers": [
{ "Description": "First CLI task",
"UserBucket":{ "S3Bucket": "datapower-bucket",
"S3Key" : "rel_agoradco_nonpd_xen.vhd"
}
} ]
}”
- Use the ec2 describe-import-image-tasks command to monitor the import progress.
aws ec2 describe-import-image-tasks –import-task-ids import-ami-fgifmh5x
- Once your import task is completed, you can use the ec2 run-instances command to create an Amazon EC2 instance from the AMI generated during the import process.
References:
Thursday, May 7, 2015
Monday, May 4, 2015
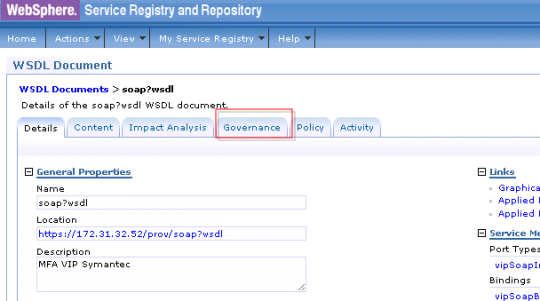
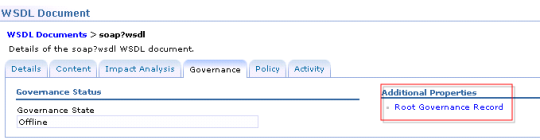
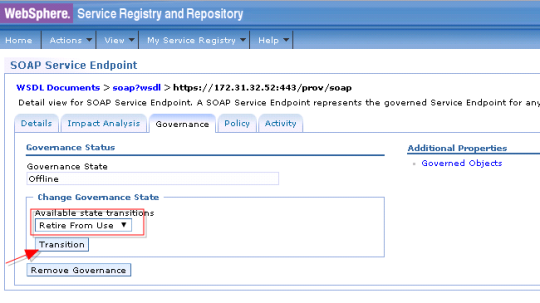
How to disable a wsdl/port type is WSRR? (82/285 technotes for 2015)
Login to WSRR –> WSDL Document –> click on the wsdl that you want to “retire” –> Governance tab –> “Retire from use” –> Transition
Top 3 vendors in smart/intelligent BPM space. (81/285 technotes for 2015)
Changing Market - iBPMs include social, analytics and cloud in their offering
For different factors for iBPMs are
- Composition of intelligent, process-centric applications
- Continuous process improvement (CPI)
- Business transformation
- Digitalized process
Appian
- what is happening right now within their organization, markets and customers, and accelerate the translation of that awareness into action and business outcomes
- social centricity
Short Comings
- does not have full CEP(Complex Event Processing) and analytics capabilities
less support for top down transformation.
Pega System
- Largest pure play vendor
- can be leveraged for large complex business scenarios
advanced operational decision management capabilities, predictive analytics and IoT integration
Short Comings
- did not focus on low end mid market
- finding resource is difficult
IBM BPM
- Steadily moving to cloud
- enabling mobile, social, cloud and big data while driving efficiency and optimization into end-to-end processes.
- starting to handle - more-agile, lightweight projects.
- leader in decision management
Short Comings
- relatively hard to configure and deploy
- customer feedback is lukewarm / tepid.
References: