An ESB Must Support the following mentioned below -
Application Awareness in ESB
Application Awareness in ESB
- Service Virtualization
- Improved Manageability - all the things below can be managed centrally
- style sheets
- security
- caching
- routing
- Monitoring and Managing messages as they flow on the bus
- Routing messages
- Converting Protocols
- Transformation
- Securing messages
- Providing connectivity to application services via open and propriety interfaces
Monitoring & Managing - log information about arrival path, contents of the msg based on filters
- ESB general monitoring
- track messages as they flow through the Enterprise - determine where time and resources are being spent
- remote monitoring of Datapower appliances - using SNMP, WSDM, WS-Management and proprietary SOAP API.
- for end to end monitoring for the ESB as well as the services is to - integrate Enterprise Monitoring software through std protocols like SNMP and ARM - like ITCAM for SOA
- ESB service level management (SLA) via monitoring - this is one of the most important
- throttle (reject) and shape(delay) traffic based on patterns below
- Prioritization
- Count Monitors
- Duration Monitors
- protects the backend application resources when.
- application latency reaches a threshold
- processing latency reaches a threshold
Routing - is required the 2 reasons mentioned below
- Quality of Service - able to prioritize some message based on the the SLA
- Support of specific functionality or affinity -
- some functionality provided in a particular version
- session may exist on a particular destination - requiring affinity based routing
- Different types of Routing
- Content based routing
- Context based routing
- Aggregation and Disaggregation
Protocol Conversion -
- need to move messages from one protocol to another
- web based scenario's are asynchronous, but back end systems are transaction oriented and want it to be synchronous. So state management responsibility is also there for the mediator.
- if Websphere ESB is used - to convert protocol and transform and route message - it in general degrades performance
Message Transformation -
Securing Messages -
Connectivity -
- XML-to-XML Transformations
- HTML/SOAP to XML Transformations
- Binary Transformations
- Content Enrichment and Filtering
Securing Messages -
- Though it has a large set of Security services - but a fairly small set of Services should be available for an ESB
- Support for standard WS-Security protocols as defined in the WS-I Basic Security Profile
- Support for credential mapping across multiple protocols and transports
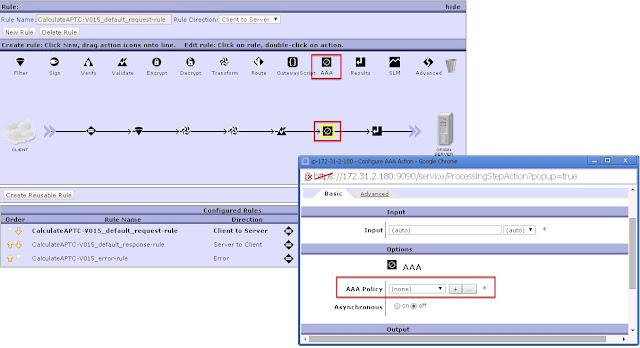
- AAA
Connectivity -
References:
Datapower Architectural Design Patterns - Integrating and Securing Services Across Domains - http://www.redbooks.ibm.com/redbooks/pdfs/sg247620.pdf